Cloud account is sometimes called as cloud credential. You need to initiate cloud credentials to access some information from your cloud resources. For example, Amazon Web Services (AWS), requires access keys and secret keys, Azure requires app registration, GCP requires service account.
To create AWS cloud credential, we need to setup and collect the following information:
AWS Cloud Credential parameters
- Account ID
- Access key / Secret key
AWS Cloud Credential's policy
- Cloud Expense: Cost & Billing policy, Report Name (Cost & Usage report)
- Cloud Safe: Security Auditing policy
- Cloud Automation: Resource policy
1. Create AWS Cloud Credential
Creating IAM user
Click link to Sign In: https://aws.amazon.com/
Click to AWS IAM console to create IAM user with name CloudSuite_{application} or any name that you want (eg. CloudSuite_expense)
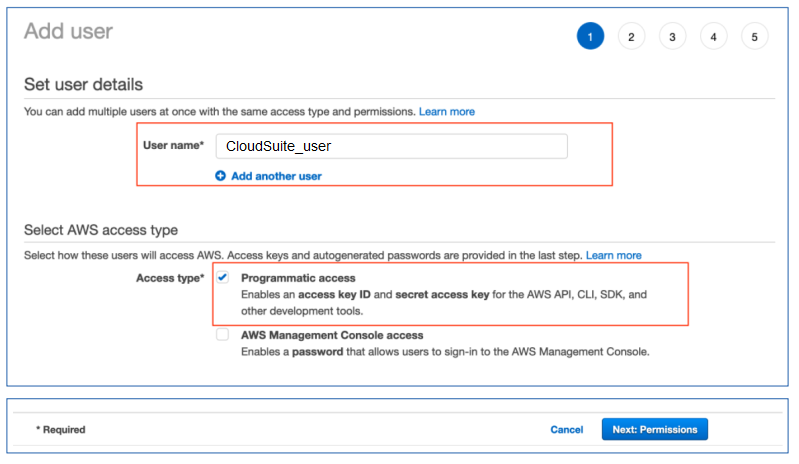
Select Programmatic access to avoid any unexpected access from Console.
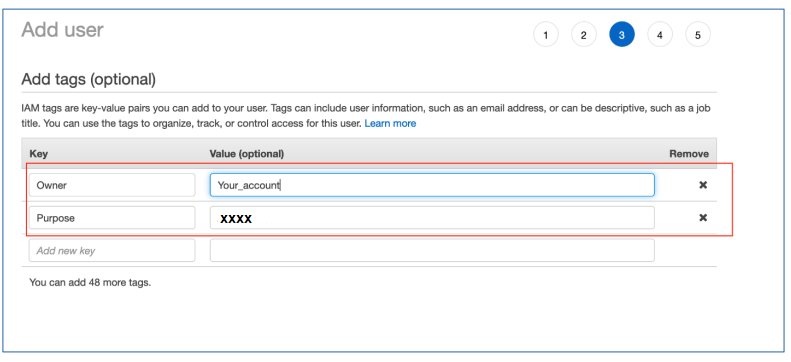
Add tag to user (optional)
- Owner: your_account (eg. hadd7)
- Purpose: CloudSuite_{Application}_Credential (eg. CloudSuite-Credential)
2. Attach the policy
We provide you the policy of Cloud Credential according to the least privileges to avoid any security issue.
| Cloud Apps | Policy |
|---|---|
| Cloud Safe | SecurityAudit, CloudSafeCustomPolicy |
| Cloud Expense | CostAndUsageListS3 (*) ReadOnlyAccess |
| Cloud Automation | ReadOnlyAccess or associated permissions depending on the templates that you use |
Security Audit
SecurityAudit is an AWS managed policy that: The security audit template grants access to read security configuration metadata. It is useful for software that audits the configuration of an AWS account.
CostAndUsageListS3
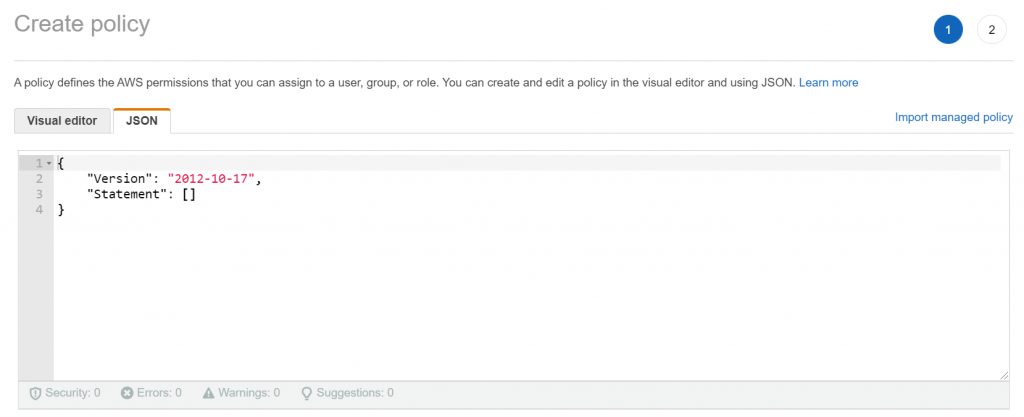
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::cloudsuite-exp-report"
}
]
}
Attach the AWS pre-defined policies which is associated with your application such as Security Audit of Cloud Safe, Read-Only of Cloud Expense, Administrator of Cloud Ops.
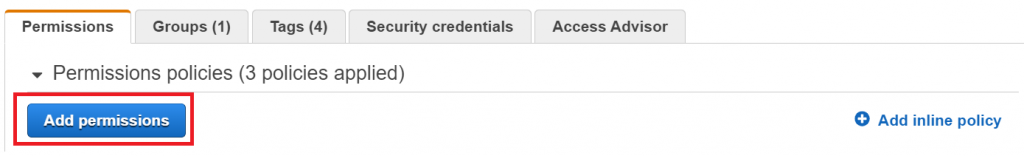
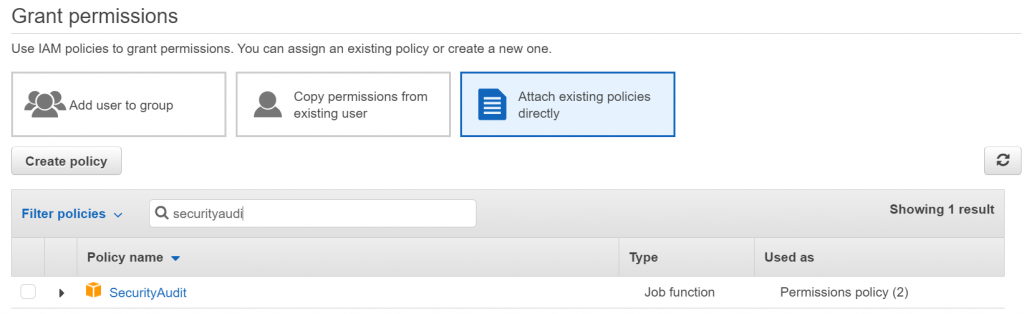
Attach added custom policy which is associated with your application by downloading the policy and paste to the inline policy
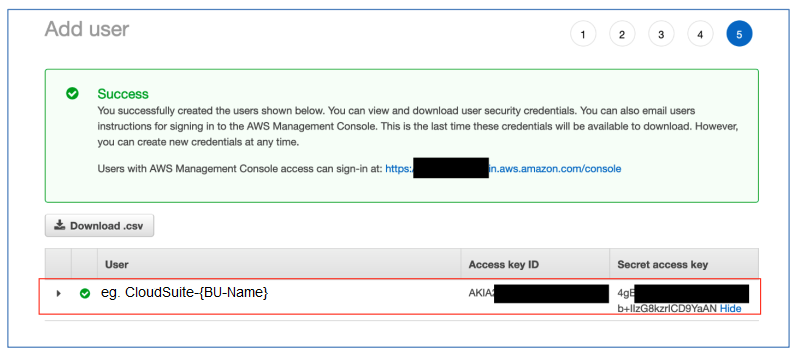
3. Copy AWS access key, secret key, account ID and report name
Access Key / Secret Key
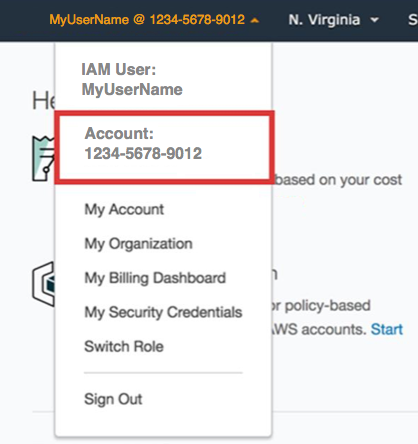
Account ID
Report Name
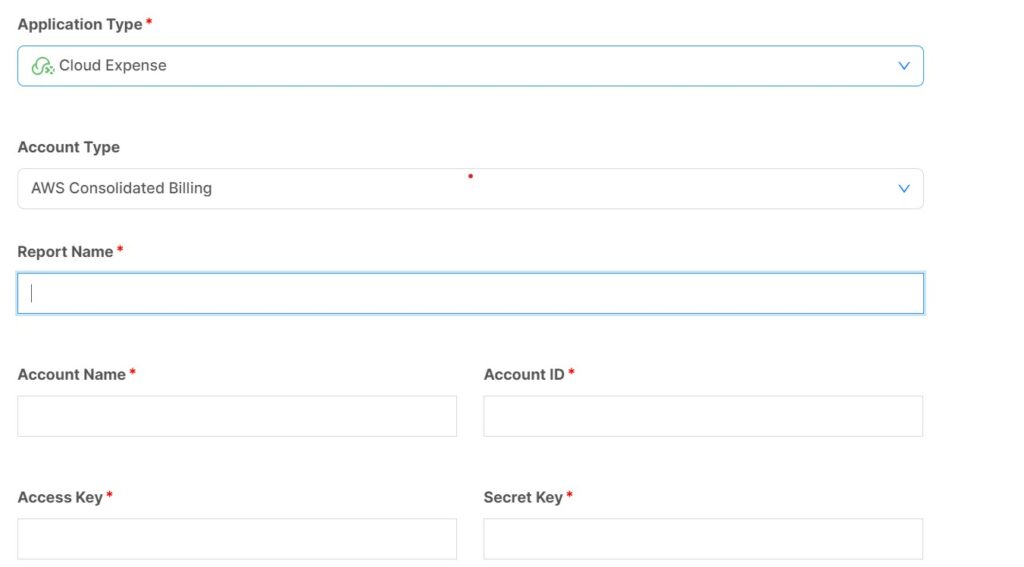
Refer to this link for the Billing report configuration: https://blog.dxcloudsuite.io/enable-aws-cost-usage-report/
4. Adding Cloud Account with parameters
Go to the Cloud Identity and register Cloud Credential:
- Account ID: *********
- AWS Access Key:
AKIA2******** - AWS Secret Key:
4gBFu************** - Report Name (or without Report Name with AWS Normal Account option)

Account type:
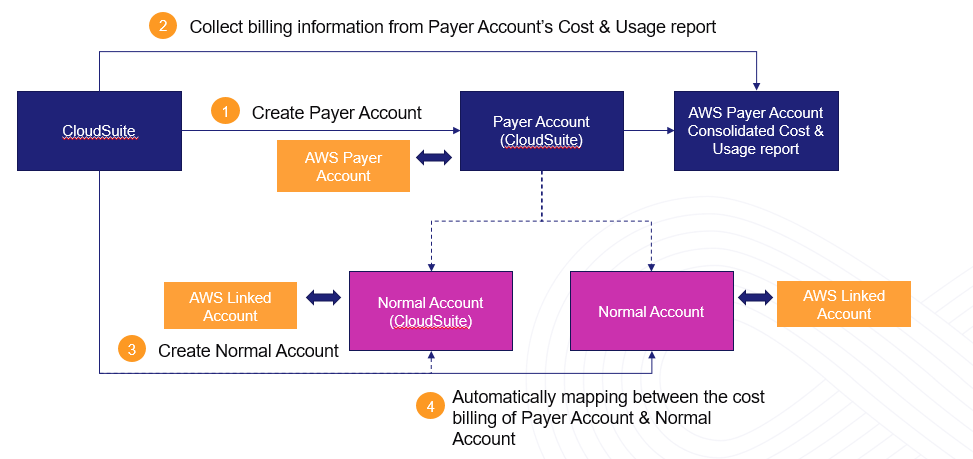
For Cloud Expense, there are two type of cloud accounts:
- Payer Account is the cloud account which is mapped with AWS Payer Account's Consolidated Cost & Usage report
- Normal Account is the cloud account which is mapped with AWS Linked Account's Cost & Usage report

The function [Automatically mapping with Payer Account] defines which option applies when you create the Normal Account.
It depends on how customer wants to deploy and link between CloudSuite cloud account and AWS payer/normal account, there are two deployment options as below:
- Option 1: Create multiple Normal Accounts and corresponding multiple ASW Cost & Usage report. It happens by default when you don't tick on the checkbox
The function [Automatically mapping with Payer Account] defines which option applies when you create the Normal Account.
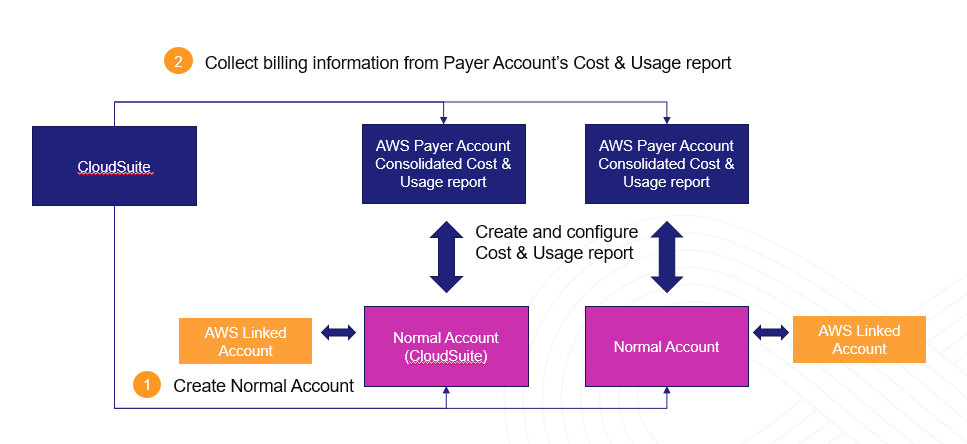
- Option 2: Create a Payer Account + AWS Consolidated Cost & Usage report and multiple Normal Accounts. It is recommended option because we don't have to create multiple Cost & Usage report for each AWS linked accounts.